The Error
I recently had the pleasure of running into this seemingly elusive "506" error when trying to migrate users that had already been configured for Skype for Business Online to a brand new On-Prem environment after configuring Hybrid. I say "elusive" because I could not find a solution on Bing or Google (yes, I started with Bing!). The actual error read as follows:
Move-CsUser : HostedMigration fault: Error=(506). Description=(The user could not be moved because there appears to be a problem with this user account. Please verify the attribute settings on the account and then try again.)
The Scenario
Let's get a good handle on what this environment looked like, and what it was currently at the time of this error, as this information is key. This organization had Hybrid Exchange setup, but all the mailboxes were homed in Exchange Online. They had also been using Skype for Business Online exclusively; there was no on-prem Skype for Business infrastructure. Lastly, Azure AD Connect was properly set up, and syncing without errors. All good and pretty!
Now, the goal here was to implement an on-prem Skype for Business deployment so that users in a particular geography could use the on-prem voice infrastructure. The plan was to implement the on-prem infrastructure, configure Hybrid for Skype for Business, and then move the users in this particular geography to the on-prem infrastructure while leaving all other users in the Online environment. Everything up to the step in which users are moved to On-Prem worked fine.
The Troubleshooting
So, Hybrid was configured, the on-prem environment worked well on its own, and the Online users were registering through the on-prem environment without a hitch. Why then, could we not simply move the users to the on-prem environment? Looking at the above error, the complaint seems to be centered around a problem with attributes. Ok, first thing, go back and ensure that your Azure AD Connect configuration is syncing successfully.
A quick look in Office 365 Admin Center verifies that the sync is happening at regular intervals, and happening successfully. Next, lets go to the actual AADC server, and make sure that the attributes for Skype for Business are all syncing successful...WAIT!!! Of course the Skype for Business attributes are not syncing! Remember, AADC was setup and configured to sync BEFORE the on-prem Skype for Business infrastructure was ever in place! Remember, one of the first things we do when installing Skype for Business Server 2015 is to extend the Schema so that all the new Skype for Business-specific attributes will be present within AD. Since AADC was installed and configured before this Schema Extension took place, AADC is not aware of these new Skype for Business attributes.
So, we go onto the AADC server, and from the START menu we find the Synchronization Service for Azure AD Connect:
Click on it to open up the GUI:
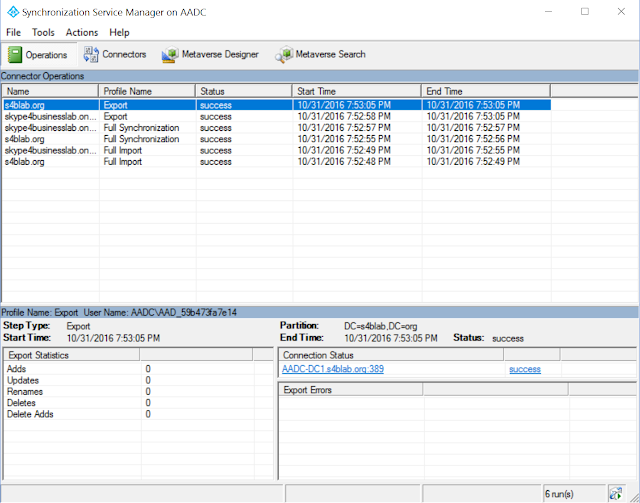
Now, let's navigate to Connectors at the top of the tool, and for each Connector (we'll do both for good measure, but highlight one at a time and perform the action), click on Refresh Schema from the list of action items on the right side of the tool:
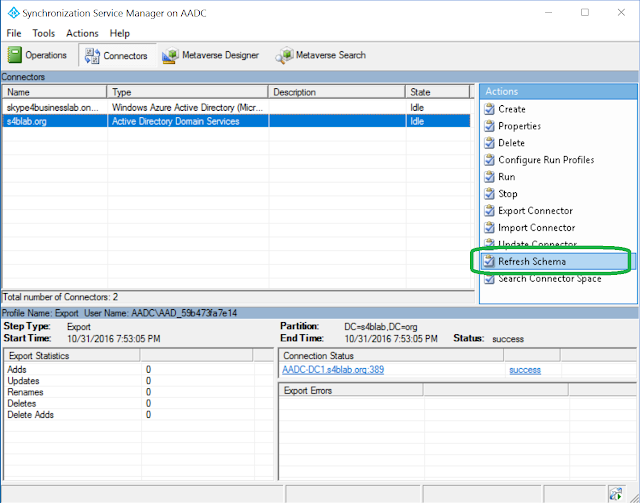
Read the warning text, and then click OK to implement the Schema Refresh:
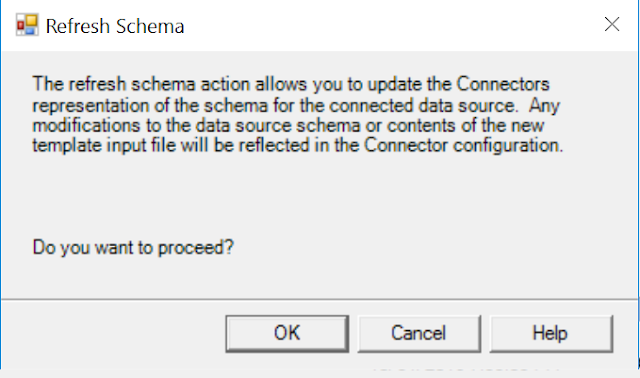
You will then need to provide credentials to connect to the Directory for the specific connector. The below image reflects that we are attempting to connect to the on-prem Active Directory, and the password must be provided. Don't forget to change the User name to a Domain Admin in your org as well; I did not do this for the below image, but did afterwards:
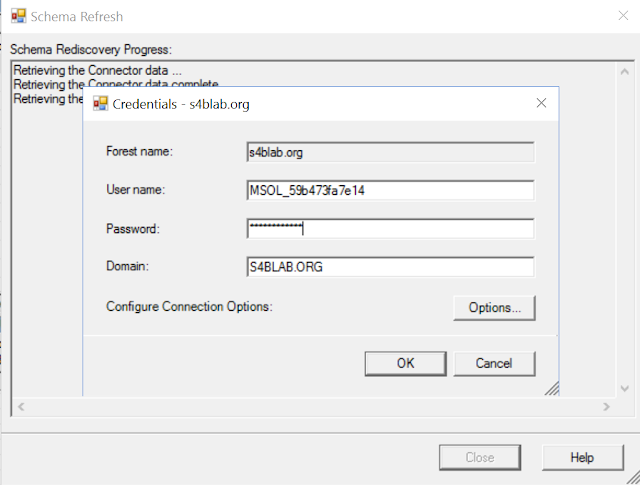
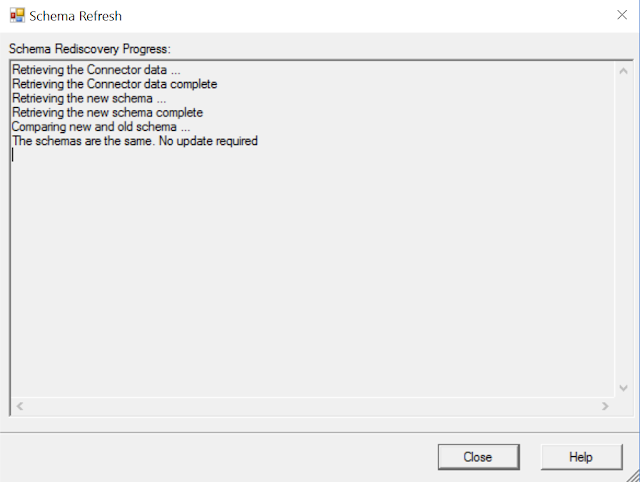
As you can see below, the Schema's are compared, and in the case of my test lab, there were no Schema updates, but in the scenario described in this blog post, you will see the Schema changes that were detected.
The Fix
Ok, once I updated the Schemas I waited for the next sync to occur from AADC, to make sure all the new attributes were synced to Skype for Business Online. However, after waiting for the successful sync, and trying the Move-CsUser operation once again, it STILL failed!
This is the point at which I put in a ticket with Microsoft through the Office 365 Admin Center. As usual, they responded very quickly. After going through the environment together for a while, the Microsoft tech zeroed in on one fact that I did not think anything about when I saw it. First we opened up Azure AD Connect, and then clicked on View Current Configuration:
Finally, something on the next screen stuck out to him. Can you guess what it is from the below image:
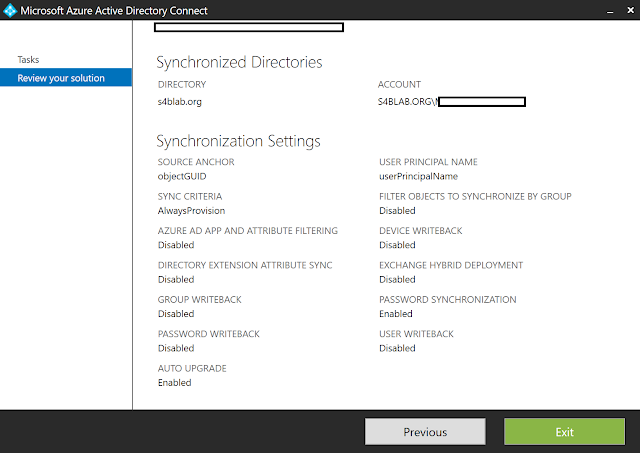
Well, if you didn't guess it, welcome to the club. It was the fact that Exchange Hybrid Deployment was disabled! Yep. EXCHANGE HYBRID.
Of course, I argued that this shouldn't matter, as this should be for Exchange Hybrid settings; there is no checkbox for Skype for Business Hybrid. At this point, the tech acknowledged that even though this field is labeled as "Exchange", it actually pertains to the environment as described above as well. Unfortunately, there was no technical documentation to back this up, at least that he knew of, but at this point I figured, "What the heck, what will it hurt to try it at this point?!" Hitting Previous in the Azure AD Connect GUI, I then clicked on Customize Synchronization Options, and then Next.
Of course, we must authenticated again:
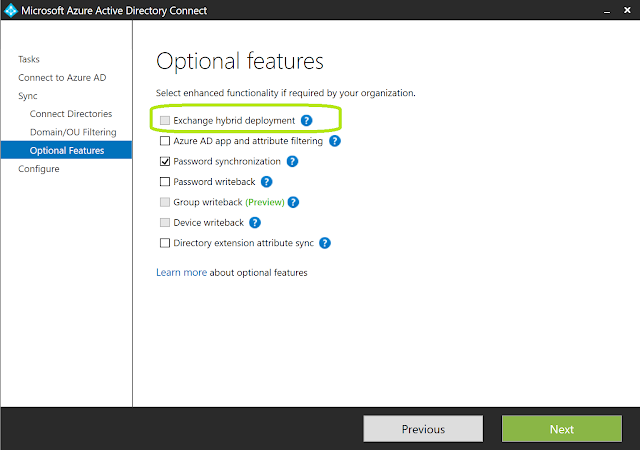
After putting in credentials for Office 365, making sure that your on-prem AD domain is already added in, and skipping on down to the Optional Features tab, you will see that the Exchange hybrid deployment checkbox is not checked. (NOTE: in my lab environment, I do not have Exchange or Skype for Business installed, so this option is Greyed out. In the real-world environment described throughout this post, this option is NOT greyed out.) Check it, and then click Next:
On the Ready to Configure screen, make sure that you leave the checkbox checked for starting a sync, and then click Configure:
When the configuration is complete, just click Exit, as seen below, and wait for the synchronization to finish. Depending on the size of your environment, the synchronization could take a while. I want to say it took at least 15 minutes to re-sync an environment of about 1,400 people with all the new attributes.
Now, I wish I had some big fancy finish to this post, but honestly, the fact is that after I enabled Exchange Hybrid Deployment in Azure AD Connect, all the needed attributes finally synced to Office 365, and I was then able to successfully move users from Online to on-Prem. Honestly, I am still a little skeptical, simply because the setting is so blatantly labeled as "EXCHANGE" Hybrid, but I suppose it wouldn't be the craziest thing I have seen from configuration settings on Microsoft products...
At any rate, if any of you find yourselves in this so-called "Reverse Hybrid" process, and get the 506 Error due to attributes being off, it is likely that your Azure AD Connect config needs to be updated to:
1. Refresh Schema
And/or
2. Enable Exchange Hybrid Deployment checkbox.
Stay techy, my friends!



























































